Wired Equivalent Privacy (WEP) is specified by IEEE 802.11 for encryption and authentication. The standard describes WEP as having two main parts. The first being the Authentication part the second being the Encryption part. The goals of WEP are:
- Access control achieved by preventing authorized users from gaining access because they do not have the correct WEP key
- Privacy is obtained by using the WEP key to encrypt the WLAN data streams and only those with the correct WEP key can decrypt them.
Figure 1 shows an example of WEP authentication:

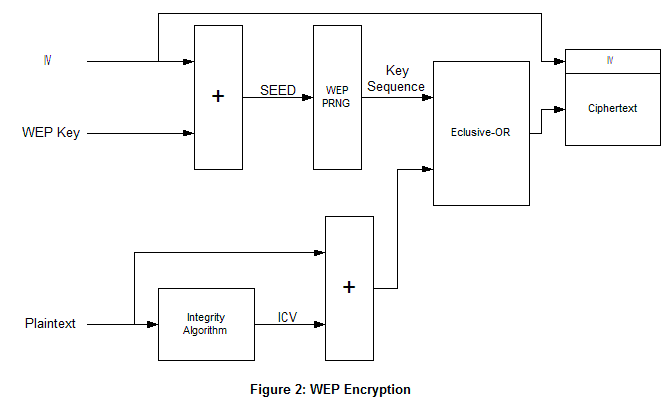
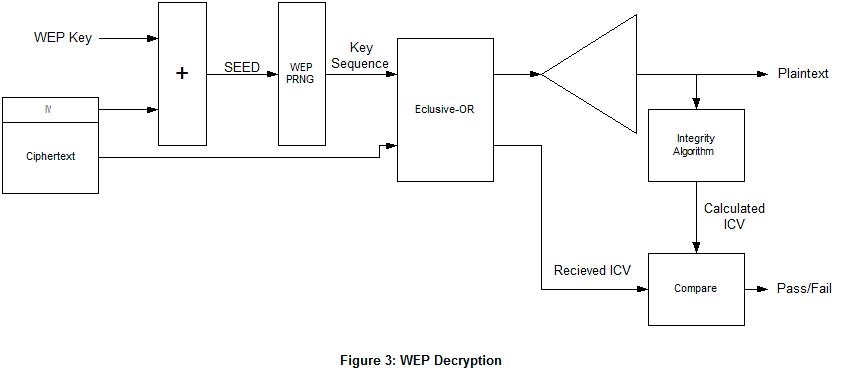
The encryption process used by WEP is Rivest Cipher 4 (RC4). There is also a Integrity algorithm CRC-32 is used on the plaintext to create the Integrity Check Value (ICV) used to protect from tampering or unauthorized data modification. Figure 2 shows the encryption algorithm and Figure 3 shows the decryption algorithm.