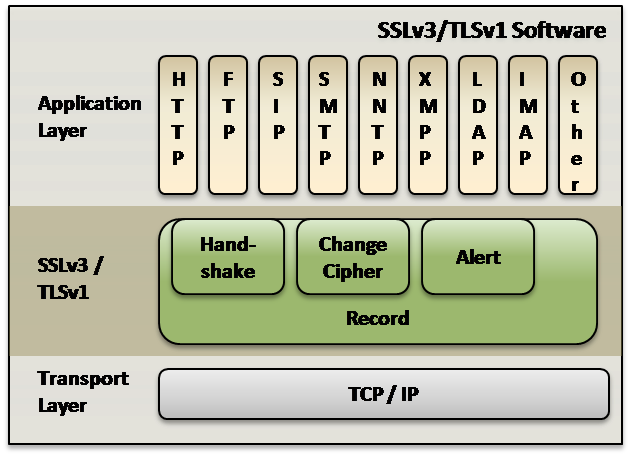
Transport Layer Security (TLS) and Secure Socket Layer (SSL) are cryptographic methods to encrypt data at the Transport Layer from end to end. These security protocols are used to secure application protocols such as HTTP, FTP, SIP, SMTP, NNTP, and XMPP. VOCAL’s software library provides Transport Layer Security version 1 (TLSv1) and Secure Socket Layer version 3 (SSLv3).
TLSv1 and SSLv3 operate at a layer between the transport and application layers. In this position multiple application layer protocols can be supported by securing the application data before sending it to the transport layer. Contact us to discuss recommended algorithms to meet your network application requirements.
TLS and SSL Sub-Protocols
The TLSv1 and SSLv3 layer consists of four sub-protocols:
- Handshake Protocol– responsible for session negotiation which consists of:
- Session Identifier – arbitrary byte sequence to identify the session state
- Peer Certificate – X.509 Certificate of peer (may be NULL)
- Compression Method – algorithm used to compress data prior to encryption
- Cipher Spec – specifies cryptographic attributes and these three cryptography protocols:
- pseudo-random function used to generate keying material
- bulk data encryption algorithm
- MAC algorithm
- Master secret – 48 byte secret shared between client and server
- is resumable – flag to indicate if the session can be used to initiate new connections
These are used to create the security parameters used by the record layer.
- Change Cipher Spec Protocol – This protocol is used to signal transitions between cipher
strategies. - Alert Protocol – This protocol allows for the use of the Alert message, these convey what the alert is as well as the severity.
- Record Protocol – This protocol using, the cipher suite information, takes the application data and encrypts it before passing it to the transport layer.
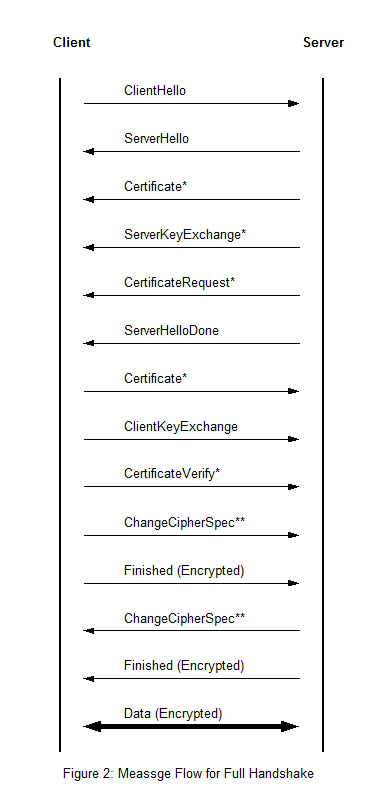
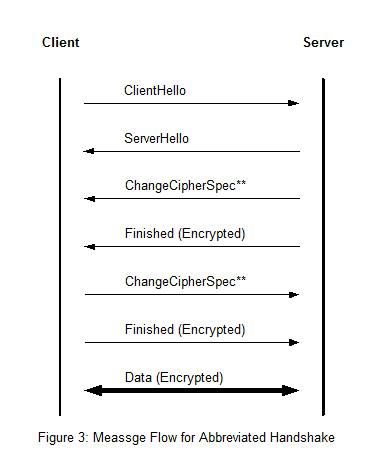
Figure 2 shows the message flow of a full handshake and Figure 3 shows an abbreviated handshake for resumption or duplication. The messages marked with a “*” are optional or depend on the situation. ChangeCipherSpec has its own protocol and is not a part of the Handshake protocol. This flow accomplishes the following tasks:
- Exchange hello messages to agree on algorithms, exchange keying material, and check for resumption of session
- Allow the client and server to agree on a pre-master secret by exchanging the needed cryptographic parameters
- Allow the client and server to authenticate themselves by exchanging certificates and cryptographic parameters
- Generate a master secret from the pre-master secret and the exchanged keying material
- Provide the record layer with security parameters
- Verify that the peers have calculated the same security parameters and that the handshake occurred without unauthorized tampering
TLS and SSL Cryptography Algorithms
TLSv1 and SSLv3 make use of multiple cryptographic algorithms that are specified in the cipher suite. Each cipher suite designates a Key Exchange algorithm, Cipher algorithm and MAC algorithm. RSA and Diffie-Hellman (DH) can be used for the key exchange. RC4, 3-DES and AES are algorithms that can be used for encryption. MAC algorithms are Message Digest 5 (MD5), SHA-1, and SHA-256. The table below shows the construction of different cipher suites. Advances in technology may affect the level of security provided by the different suites. Please contact us for recommended configurations.
Cipher Suite Key Cipher MAC
Exchange
TLS_NULL_WITH_NULL_NULL NULL NULL NULL
TLS_RSA_WITH_NULL_MD5 RSA NULL MD5
TLS_RSA_WITH_NULL_SHA RSA NULL SHA
TLS_RSA_WITH_NULL_SHA256 RSA NULL SHA256
TLS_RSA_WITH_RC4_128_MD5 RSA RC4_128 MD5
TLS_RSA_WITH_RC4_128_SHA RSA RC4_128 SHA
TLS_RSA_WITH_3DES_EDE_CBC_SHA RSA 3DES_EDE_CBC SHA
TLS_RSA_WITH_AES_128_CBC_SHA RSA AES_128_CBC SHA
TLS_RSA_WITH_AES_256_CBC_SHA RSA AES_256_CBC SHA
TLS_RSA_WITH_AES_128_CBC_SHA256 RSA AES_128_CBC SHA256
TLS_RSA_WITH_AES_256_CBC_SHA256 RSA AES_256_CBC SHA256
TLS_DH_DSS_WITH_3DES_EDE_CBC_SHA DH_DSS 3DES_EDE_CBC SHA
TLS_DH_RSA_WITH_3DES_EDE_CBC_SHA DH_RSA 3DES_EDE_CBC SHA
TLS_DHE_DSS_WITH_3DES_EDE_CBC_SHA DHE_DSS 3DES_EDE_CBC SHA
TLS_DHE_RSA_WITH_3DES_EDE_CBC_SHA DHE_RSA 3DES_EDE_CBC SHA
TLS_DH_anon_WITH_RC4_128_MD5 DH_anon RC4_128 MD5
TLS_DH_anon_WITH_3DES_EDE_CBC_SHA DH_anon 3DES_EDE_CBC SHA
TLS_DH_DSS_WITH_AES_128_CBC_SHA DH_DSS AES_128_CBC SHA
TLS_DH_RSA_WITH_AES_128_CBC_SHA DH_RSA AES_128_CBC SHA
TLS_DHE_DSS_WITH_AES_128_CBC_SHA DHE_DSS AES_128_CBC SHA
TLS_DHE_RSA_WITH_AES_128_CBC_SHA DHE_RSA AES_128_CBC SHA
TLS_DH_anon_WITH_AES_128_CBC_SHA DH_anon AES_128_CBC SHA
TLS_DH_DSS_WITH_AES_256_CBC_SHA DH_DSS AES_256_CBC SHA
TLS_DH_RSA_WITH_AES_256_CBC_SHA DH_RSA AES_256_CBC SHA
TLS_DHE_DSS_WITH_AES_256_CBC_SHA DHE_DSS AES_256_CBC SHA
TLS_DHE_RSA_WITH_AES_256_CBC_SHA DHE_RSA AES_256_CBC SHA
TLS_DH_anon_WITH_AES_256_CBC_SHA DH_anon AES_256_CBC SHA
TLS_DH_DSS_WITH_AES_128_CBC_SHA256 DH_DSS AES_128_CBC SHA256
TLS_DH_RSA_WITH_AES_128_CBC_SHA256 DH_RSA AES_128_CBC SHA256
TLS_DHE_DSS_WITH_AES_128_CBC_SHA256 DHE_DSS AES_128_CBC SHA256
TLS_DHE_RSA_WITH_AES_128_CBC_SHA256 DHE_RSA AES_128_CBC SHA256
TLS_DH_anon_WITH_AES_128_CBC_SHA256 DH_anon AES_128_CBC SHA256
TLS_DH_DSS_WITH_AES_256_CBC_SHA256 DH_DSS AES_256_CBC SHA256
TLS_DH_RSA_WITH_AES_256_CBC_SHA256 DH_RSA AES_256_CBC SHA256
TLS_DHE_DSS_WITH_AES_256_CBC_SHA256 DHE_DSS AES_256_CBC SHA256
TLS_DHE_RSA_WITH_AES_256_CBC_SHA256 DHE_RSA AES_256_CBC SHA256
TLS_DH_anon_WITH_AES_256_CBC_SHA256 DH_anon AES_256_CBC SHA256