Automatic Speaker Verification (ASV) can be been used as a biometric authentication technique. The physical characteristics of a person’s vocal tract and the intonation of their speech provides a unique set of features that can be used to verify their identity. However, speaker verification systems can be subject to malicious attacks in order to fool (spoof) the system in providing a false positive on authentication. There are four types of spoofing attacks: impersonation, replay, speech synthesis and voice conversion.
An impersonation attack occurs at the microphone level is when a person changes how they talk to mimic the speech characteristics of the legitimate user. A non-professional is able to fool an ASV system if the impostor’s natural voice has similar features. More effective microphone level attacks are replay attacks, which uses recorded of the person of interest. Given that smart phones have the ability to obtain high-quality recordings, it makes easy to perform this type of attack. Splicing together different recordings allows attackers to bypass text-dependent ASV systems.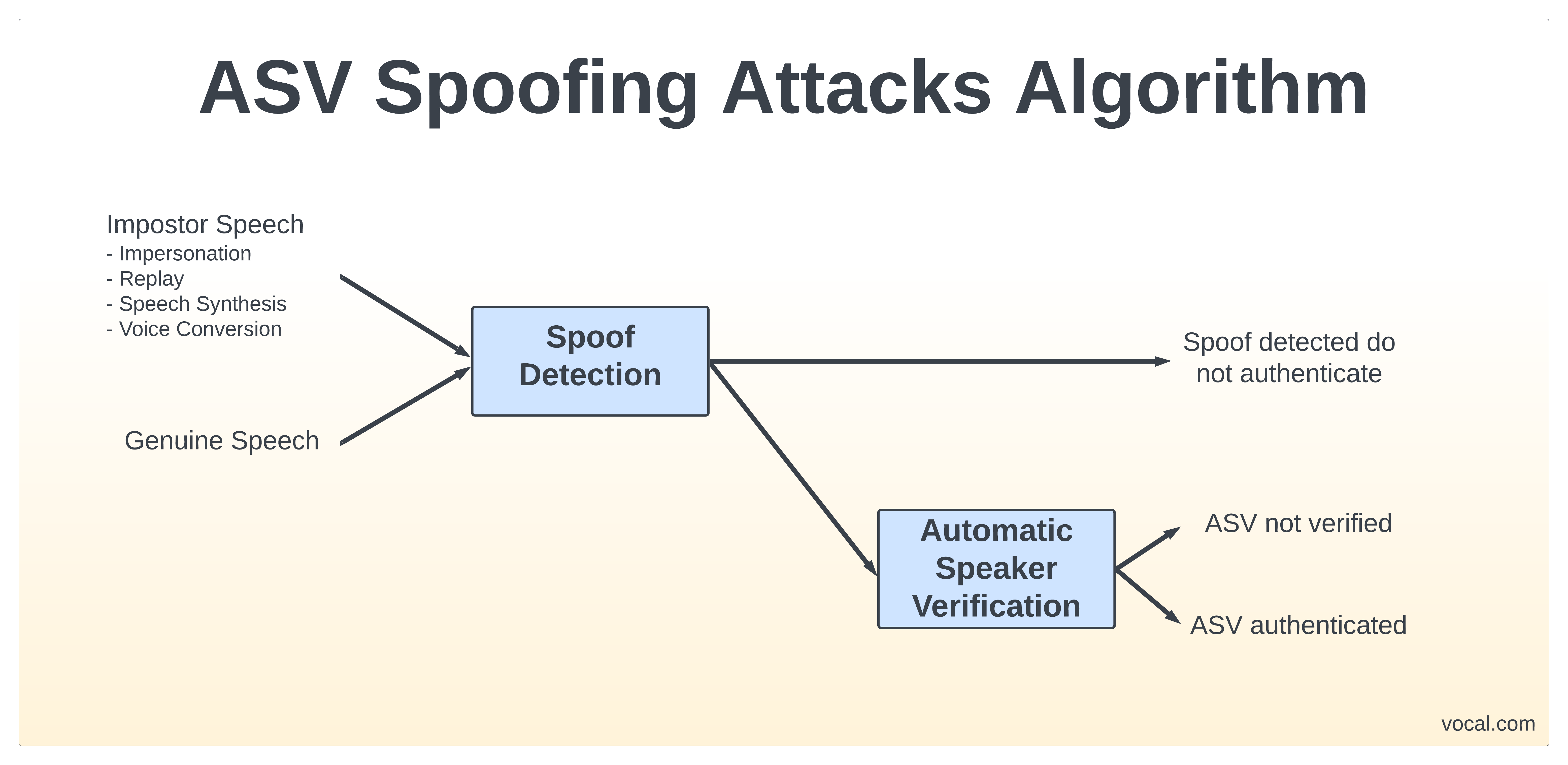
Speech synthesis generates artificial speech from a given set of text. Speech synthesis has gained attention most recently for being able to generate high quality artificial music of singers, such as Amy Winehouse. However, they can also be used to spoof text-independent and text-dependent ASVs. With recent advances in the machine learning and deep neural networks (DNN), models which generate accurate speech features can be trained using a small data set of recorded audio. Voice conversion is similar to that of speech synthesis, but instead of using text as input, the impostor’s natural voice can be used to generate artificial speech. Again, advances in machine learning have allowed for the mapping of speech features between speakers to be accurate and computationally efficient enough to make ASV vulnerable to these types of attacks. [1]
VOCAL Technologies has been doing speech signal processing for over 35 years. Spoofing detection software can be used as a front-end to ASV system to help detect when ASV spoofing attacks occur. Please contact us for more information.
VOCAL’s solution is available for the above platforms. Please contact us for specific supported platforms.

